In the vast, data-hungry world of underwater monitoring and naval surveillance, researchers are diving deep to enhance security and efficiency in communication. A recent study, led by Jinsu Ahn from the School of Electronic and Electrical Engineering at Kyungpook National University in South Korea, has shed light on a novel authentication protocol for underwater wireless sensor networks (UWSNs). Published in the journal ‘Applied Sciences’ (which translates to ‘Applied Sciences’), the research tackles the unique challenges posed by the underwater environment, where bandwidth is limited, delays are long, and nodes are physically exposed to potential threats.
So, what’s the big deal? Well, imagine a network of sensors deployed underwater, tirelessly collecting data for marine monitoring or coastal surveillance. These sensors need to communicate securely, ensuring that the data they transmit isn’t intercepted or tampered with. Traditional authentication methods often fall short in this harsh, unpredictable environment. That’s where Ahn’s research comes in.
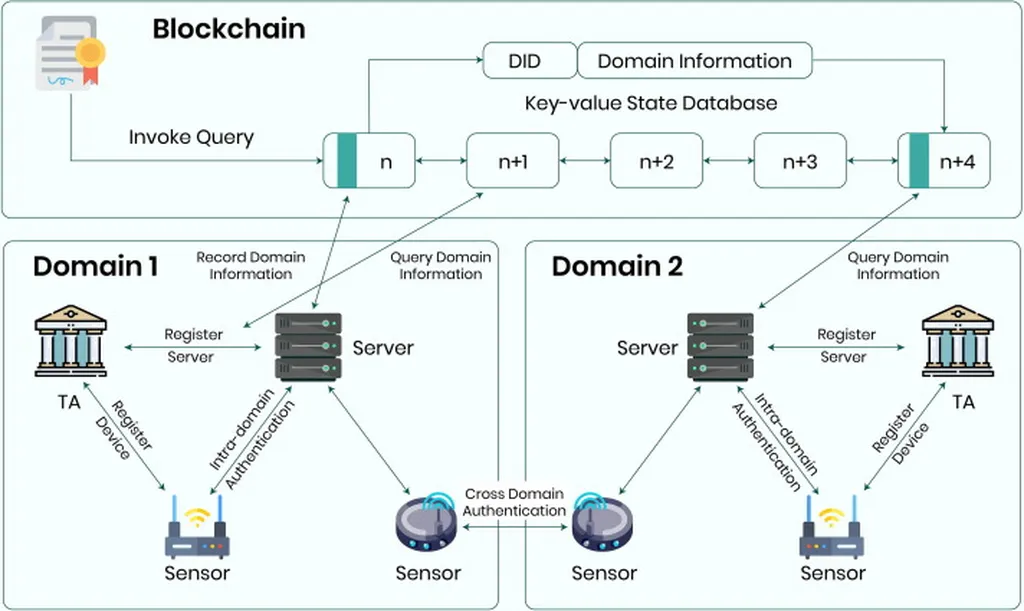
The study builds upon a previously proposed protocol by Jain and Hussain, identifying its vulnerabilities to physical capture, replay, and denial-of-service (DoS) attacks. Ahn and his team propose a new protocol that leverages Physically Unclonable Functions (PUFs), unique physical fingerprints of electronic devices, to enhance security. “Our design relies on lightweight symmetric primitives (one-way hash and XOR) and uses a fuzzy extractor to support stable PUF-based key material,” Ahn explains. In simpler terms, they’ve developed a robust, efficient method for sensors to authenticate each other and agree on a session key, ensuring secure communication.
One of the standout features of this new protocol is its ability to handle intermittent link disruptions, a common occurrence in underwater communication. Ahn’s team introduces a lightweight continuous authentication procedure, enabling fast re-authentication when connections drop. This is a significant improvement, as it ensures that data transmission isn’t interrupted for long periods, even in the challenging underwater environment.
The security of the protocol was rigorously evaluated using BAN logic, the Real-or-Random (ROR) model, and the Scyther tool. The results are promising, demonstrating a practical balance between security and efficiency. The protocol boasts a computational cost of 5.972 ms per mutual authentication and a communication overhead of 1152 bits, making it suitable for resource-constrained UWSN deployments.
So, what does this mean for the maritime industry? The implications are substantial. Enhanced security in underwater communication can lead to more reliable data collection for marine research, improved monitoring of underwater infrastructure, and more effective naval surveillance. This could translate to better protection of coastal areas, more efficient management of marine resources, and enhanced safety for underwater operations.
Moreover, the commercial opportunities are vast. Companies developing underwater sensor networks can integrate this protocol into their systems, offering clients enhanced security and reliability. This could open up new markets and drive innovation in the maritime sector. As Ahn puts it, “Our protocol supports a practical security–efficiency trade-off for resource-constrained UWSN deployments,” highlighting its potential for real-world applications.
In conclusion, Ahn’s research represents a significant step forward in securing underwater communication. By addressing the unique challenges of the underwater environment, this protocol paves the way for more reliable, efficient, and secure data transmission. As the maritime industry continues to evolve, such advancements will be crucial in harnessing the full potential of underwater technology.